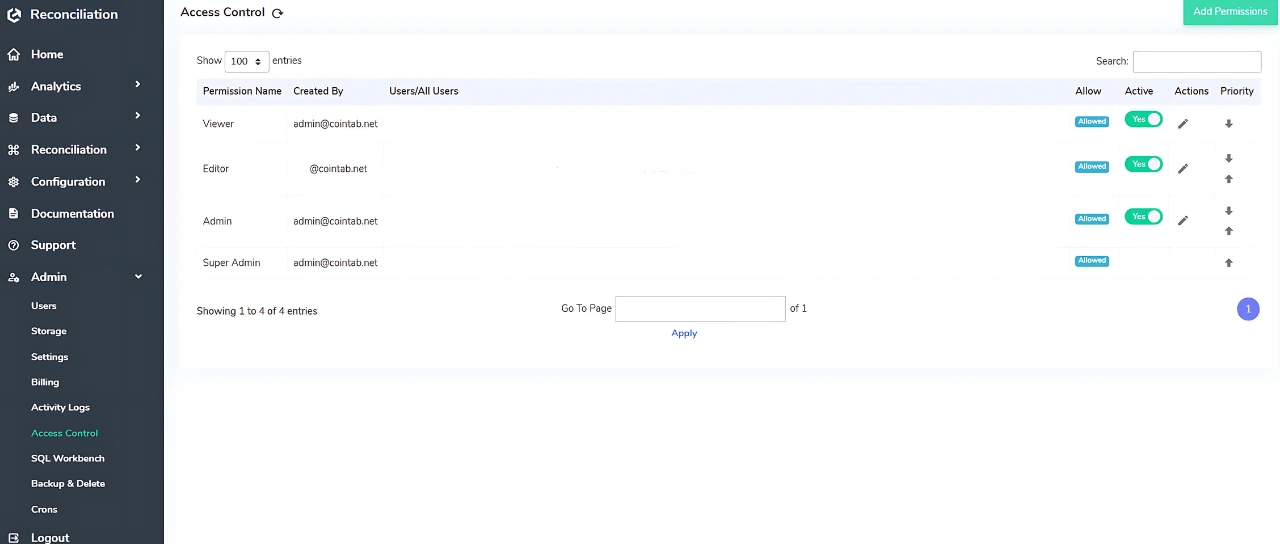
Introduction to Access Control Feature
Ensuring data security and confidentiality is a top priority in financial reconciliation. Cointab’s Access Control feature is designed to safeguard sensitive financial information while allowing administrators to maintain precise control over data access. This feature enables organizations to define user permissions granularly, ensuring that each team member interacts only with the data relevant to their role.
Key Features of Access Control
Role-Based Access Permissions
- Assign access rights based on organizational roles.
- Restrict access to sensitive financial data and operations.
- Ensure compliance with internal security policies and regulations.
Granular Action-Based Controls
- Enable users to view, edit, create, or delete data templates.
- Define permissions for reconciliation execution and auditing.
- Control access to dashboards, data backups, and system configurations.
Configurable User Access Levels
- Adjust permissions through the Configuration section in Cointab.
- Collaborate with Data Analysts (DAs) for tailored access settings.
- Align permissions with organizational hierarchy and operational requirements.
Enhanced Security for Sensitive Operations
- Protect financial records from unauthorized modifications.
- Implement multi-layered security measures for high-risk operations.
- Monitor and manage user activities to prevent unauthorized access attempts.
Use Cases Across Departments and Industries
SaaS
- Define role-based access for customer data and subscription records.
- Secure sensitive operational data from unauthorized handling.
Logistics & Supply Chain
- Control access to vendor payment details and procurement reports.
- Restrict order fulfillment and invoicing data to designated teams.
Financial Institutions
- Restrict reconciliation approvals to authorized personnel.
- Ensure only designated users can modify financial data.
E-commerce
- Limit access to sales and transaction records to key stakeholders.
- Prevent unauthorized modifications to inventory and payment records.
Discover How Source Data Automation Can Enhance Your Workflow. Book a Demo!
How Access Control Feature Works
01.
Navigate to Configuration
Access the ‘Configuration’ section in Cointab to manage user roles and permissions.
02.
Define User Roles
Assign predefined roles or create custom roles based on team requirements.
03.
Set Permissions
Specify permissions for each role, such as data viewing, editing, reconciliation, and report generation.
04.
Restrict Access to Sensitive Data
Limit access to critical functions like template deletion, financial report modifications, and system settings.
05.
Save and Apply Changes
Confirm and implement access control settings to enforce security policies.
“Organizations using batch processing and advanced executors saw a 40% reduction in reconciliation cycle time."
– Reconciliation Trends Report, 2024
Benefits for Your Organization
For Analysts
- Ensures clear access boundaries for efficient workflow management.
- Prevents accidental modifications to critical financial data.
For Managers
- Simplifies user management with structured role-based access.
- Enhances accountability and reduces security risks.
For Leadership Teams
- Strengthens organizational security posture.
- Ensures compliance with financial data protection regulations.